SQL INJECTION
Some Basics First
What is SQL
-
SQL stands for Structured Query Language, designed for maintaining data in a Relational Database Management System(RDBMS): a database system which stores data in rows and columns
-
A transaction in SQL is known as Query
Some SQL Commands
-
SELECT
- Returns the desired columns from a table based on conditions if specified
-
SELECT (NAME,PHONE_NUMBER ) FROM DIRECTORY
-
WHERE
- Imposes conditions in a Query
-
SELECT (NAME,PHONE_NUMBER) FROM DIRECTORY WHERE NAME= "DHAMAN ATTARWAL" -
Two or more Conditions can be imposed at a time using AND,OR, NOT keywords
-
SELECT (NAME,PROFESSION) FROM DIRECTORY WHERE NAME="MUDI_JI" AND PROFESSION="TEA_SELLER"
-
UNION
- Adds data from two tables in vertical fashion as long as number of columns in both the tables is same. . .
-
SELECT (HOUR) FROM TIME UNION SELECT (MIN) FROM TIME
-
ERROR:SELECT(HOUR)FROM TIME UNION SELECT(MIN,SEC) FROM TIME
-
DROP
- Deletes a table and its content from a database
-
DROP TABLE DIRECTORY
- TRUNCATE
- Unlike DROP, this only deletes the contents of the database leaving an empty table as it is.
-
TRUNCATE TABLE DIRECTORY
sOME IMPORTANT SYMBOLS
-
' (COMMA) - HACK
-
-- - COMMENT
-
; - eND OF STATEMENT
-
*, % - WILD CARDS
SQL INJECTION
In simple terms, it’s injection/addition where data provided by user is included in a SQL query such that part of user’s input treated as an sql code.
Example:
Entering password as ‘ OR 1=1--
Injection mechanisms
- First Order Injection
- Injection thorugh user Inputs
- Injection through server variables
- Injection through cookies
- Second Order Injection
Injection Through User Variables
SELECT * FROM USERS where USER="admin" AND PASSWORD="" OR 1=1--AND PHONE_NUMBER=<RANDOM_NUMBERS>SELECT * FROM USERS where USER="+req.body.user+" AND PASSWORD="+req.body.pass+" AND PHONE_NUMBER="+req.body.phn";
/*CORRECT: SELECT * FROM USERS where USER="admin" AND PASSWORD="password" AND PHONE_NUMBER=100*/
SECOND ORDER INJECTION
When Data in the Database can be altered by a injection attack then , it is classified under a Second Order Attack
A very simple example is a register and reset password system which present in almost every web page
Let's suppose we have an account in a web site , using SQL to store data, with username: injection and we need to change the password without knowing the original password
Step 1: We Register in the website using the username as injection" -- and a random string as temp password
Now we would have users in the database with username injection and injection" --
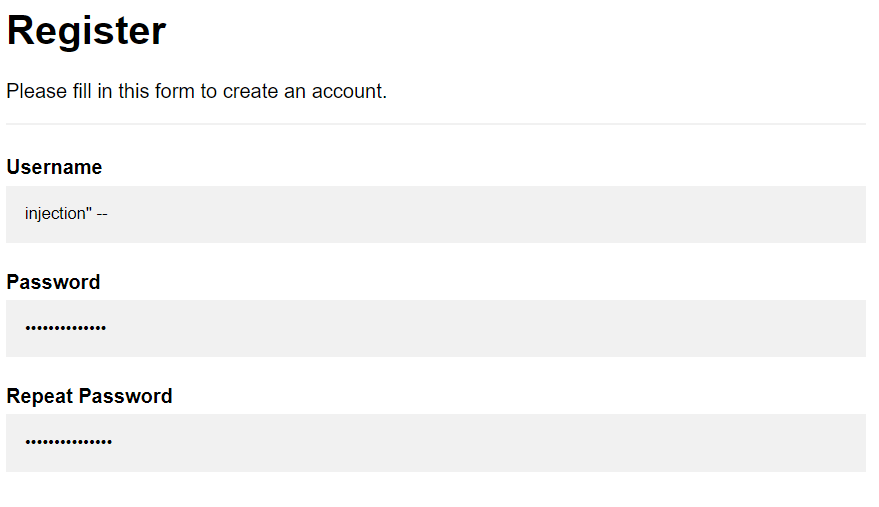
Next: We would go to the reset password page and reset the password for injection" --
For this, we would use
- username : injection" -- (pre-entered)
- old password: a random string
- new password: password which we want to set for username injection
On doing this we would change the password for username injection, lets see how this would work...
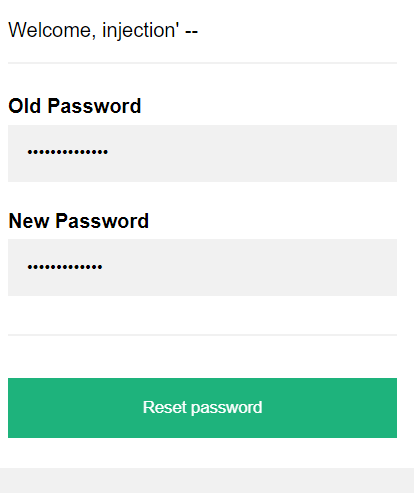
When we try to reset the password using , a command similar to this would be running
UPDATE ? SET PASSWORD="<NEW_PASSWORD>" WHERE USERNAME="<USERNAME>" AND PASSWORD="<OLD_PASSWORD>"Which would be equivalent to in our example:
UPDATE ? SET PASSWORD="hello" WHERE USERNAME="injection" -- " AND PASSWORD="<OLD_PASSWORD>"
--THIS IS EQUIVALENT TO
UPDATE ? SET PASSWORD="hello" WHERE USERNAME="injection"And so we were able to change the password of user: injection without knowing his password
Attack intent
-
Extracting data
-
adding or modifying data
-
bypassing authentication
-
priviledge escaltion
Thank You 😄